

Edition 19.0
Abstract
Mono-spaced Bold
To see the contents of the filemy_next_bestselling_novelin your current working directory, enter thecat my_next_bestselling_novelcommand at the shell prompt and press Enter to execute the command.
Press Enter to execute the command.Press Ctrl+Alt+F2 to switch to a virtual terminal.
mono-spaced bold. For example:
File-related classes includefilesystemfor file systems,filefor files, anddirfor directories. Each class has its own associated set of permissions.
Choose → → from the main menu bar to launch Mouse Preferences. In the Buttons tab, select the Left-handed mouse check box and click to switch the primary mouse button from the left to the right (making the mouse suitable for use in the left hand).To insert a special character into a gedit file, choose → → from the main menu bar. Next, choose → from the Character Map menu bar, type the name of the character in the Search field and click . The character you sought will be highlighted in the Character Table. Double-click this highlighted character to place it in the Text to copy field and then click the button. Now switch back to your document and choose → from the gedit menu bar.
Mono-spaced Bold Italic or Proportional Bold Italic
To connect to a remote machine using ssh, typessh username@domain.nameat a shell prompt. If the remote machine isexample.comand your username on that machine is john, typessh john@example.com.Themount -o remount file-systemcommand remounts the named file system. For example, to remount the/homefile system, the command ismount -o remount /home.To see the version of a currently installed package, use therpm -q packagecommand. It will return a result as follows:package-version-release.
Publican is a DocBook publishing system.
mono-spaced roman and presented thus:
books Desktop documentation drafts mss photos stuff svn books_tests Desktop1 downloads images notes scripts svgs
mono-spaced roman but add syntax highlighting as follows:
package org.jboss.book.jca.ex1;
import javax.naming.InitialContext;
public class ExClient
{
public static void main(String args[])
throws Exception
{
InitialContext iniCtx = new InitialContext();
Object ref = iniCtx.lookup("EchoBean");
EchoHome home = (EchoHome) ref;
Echo echo = home.create();
System.out.println("Created Echo");
System.out.println("Echo.echo('Hello') = " + echo.echo("Hello"));
}
}Note
Important
Warning
Fedora and the component OpenSSH_Guide. The following link automatically loads this information for you: http://bugzilla.redhat.com/.
Summary field.
Description field and give us the details of the error or suggestion as specifically as you can. If possible, include some surrounding text so we know where the error occurs or the suggestion fits.
Document URL: Section number and name: Error or suggestion: Additional information:
rpm -qa | grep openssh command. The output shown here may differ slightly from your output:
$ rpm -qa | grep openssh openssh-clients-6.1p1-6.fc18.x86_64 openssh-server-6.1p1-6.fc18.x86_64 openssh-6.1p1-6.fc18.x86_64
ssh -V (upper-case 'V') command as another way to find out the installed version:
$ ssh -V OpenSSH_6.1p1, OpenSSL 1.0.1e-fips 11 Feb 2013
yum command. Perform the following command as the root user and follow the instructions to install openssh:
# yum install openssh
sshd server on the target machine. This section provides a list of the most common tools and commands, briefly describes their function, and shows the Fedora package that provides each tool.
scp - copies files between hosts on a network. It uses ssh for data transfer, and uses the same authentication and provides the same security as ssh. Provided by the openssh-clients package.
sftp - an interactive file transfer program, similar to ftp, but performs all operations over an encrypted ssh channel. It can also use many other features of ssh, such as public key authentication and compression. Provided by the openssh-clients package.
slogin - a symbolic link to the ssh command. Provided by the openssh-clients package.
ssh - the main client program, used for logging into a remote machine and for executing commands on a remote machine. Intended to replace rlogin and rsh, it provides a secure and encrypted channel between two hosts over a network. Also used as a subsystem to other commands listed here. When using ssh, the key exchange and encryption is fully established before credentials (such as username and password) are transmitted. Provided by the openssh-clients package.
ssh-add - adds cryptography and digital signature algorithm (RSA and DSA) identities to the ssh-agent authentication agent. Provided by the openssh-clients package.
ssh-agent - a program to hold private keys used for public key authentication. The idea is that ssh-agent is started in the beginning of a session, and all other windows or programs are started as clients to it. Provided by the openssh-clients package.
ssh-copyid - a script that uses ssh to log into a remote machine and installs your own public key into a remote machine's list of authorized keys. This action provides the ability for future logins with key-based authentication. Provided by the openssh-clients package.
ssh-keygen - a utility that can generate, manage and convert authentication keys. Provided by the openssh package.
ssh-keyscan - a utility for gathering the public ssh host keys of a number of hosts. It can contact several hosts in parallel and is very fast in scanning a collection of hosts for their host keys. Provided by the openssh-clients package.
password1, is clearly displayed in the data stream. This could easily expose the password to anybody analyzing the raw data on the network, leaving a host and its services vulnerable to attack.
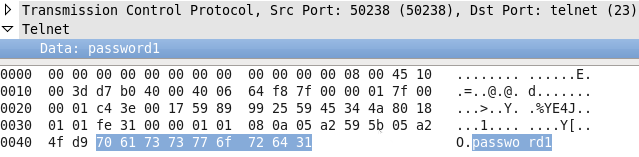
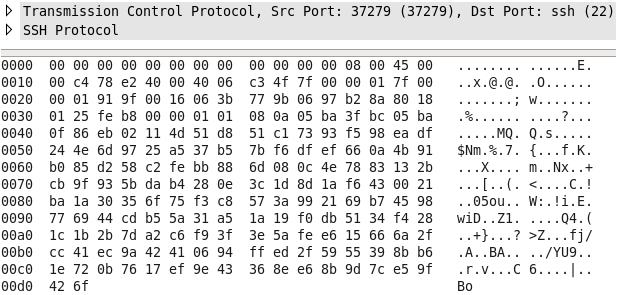
telnet and rlogin are considered insecure and outdated. Providing encryption before credentials are sent, OpenSSH can allow for stronger security when communicating over any network, but most importantly over unknown, or untrusted ones.
/etc/ssh/ssh_config. Open it with your favorite text editor to see the available options. Changes to this file are not necessary for most common uses of ssh and its server component, sshd; however, to change an option, either comment out the option (with a '#' symbol at the front of the line) to disable the option, or remove the '#' symbol at the start of the line and add an argument to enable the option to your specification.
man ssh_config) contains all available options and the effect they have on the system.
ssh command. Line numbers have been added here to help explain the actions taken.
1. [user1@localhost ~]$ ssh foo.example.com 2. The authenticity of host 'foo.example.com (10.0.0.1)' can't be established. 3. RSA key fingerprint is eb:63:02:da:88:e5:a6:fc:71:31:15:0b:cd:56:5d:3f. 4. Are you sure you want to continue connecting (yes/no)? yes 5. Warning: Permanently added 'foo.example.com,10.0.0.1' (RSA) to the list of known hosts. 6. user1@foo.example.com's password: ********* 7. [user1@foo ~]$
user1 user on the client system is initiating an SSH connection to a server with the ssh command. The server's domain name is foo.example.com, but its IP address (10.0.0.1) could be used instead.
~/home/user1/.ssh/known_hosts file. If none exist for this host, as occurs in the above example, the user is then prompted, after displaying the fingerprint, whether or not to add this record in the same known_hosts file by entering yes or no.
user1@foo.example.com is entered.
@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that the RSA host key has just been changed. The fingerprint for the RSA key sent by the remote host is eb:62:1a:da:38:f5:e6:ec:10:31:17:0b:cf:56:5d:3f. Please contact your system administrator. Add correct host key in /home/user1/.ssh/known_hosts to get rid of this message. Offending key in /home/user/.ssh/known_hosts:11 RSA host key for foo.example.com has changed and you have requested strict checking. Host key verification failed.
/etc/ssh/sshd_config file. It is important to understand the settings in the file, however, as failure to properly configure OpenSSH could lead to your system being vulnerable to attack.
/etc/ssh/sshd_config you will see several settings (and some you will not see) for setting up OpenSSH as a service. Information on all possible choices within the /etc/ssh/sshd_config can be found by man sshd_config.
/etc/ssh/sshd_config choices to address include the following:
yes Enables access with password and public key |
no Disables all direct remote logins as root |
without-password Allows access with public key authentication only |
forced-commands-only Allows access with public key authentication and only runs configured commands from ~/.ssh/authorized_keys (in the form of: allowed-command-name ssh-dsa public-key-string) |
no.
aes128-ctr,blowfish-cbc. The supported ciphers for Protocol 2 are “3des-cbc”, “aes128-cbc”, “aes192-cbc”, “aes256-cbc”, “aes128-ctr”, “aes192-ctr”, “aes256-ctr”, “arcfour128”, “arcfour256”, “arcfour”, “blowfish-cbc”, and “cast128-cbc”.
Important
sshd service after editing the configuration files before the settings take place.
/etc/ssh/sshd_config. The following commands should be modified to activate PKI authentication:
PubkeyAuthentication - Uncomment and set to yes. |
AuthorizedKeysFile - Uncomment this as well and make sure it is set to .ssh/authorized_keys. |
Important
sshd service after editing the configuration files before the settings take place.
~/.ssh/authorized_keys the system will try to authenticate them using that key before asking for a password. Want to require the key and not allow users to authenticate with a password? Just change PasswordAuthentication to no and after restarting the sshd service your system should only let people login using their PKI certificates.
| Revision History | ||||
|---|---|---|---|---|
| Revision 0.2-1 | Sun Apr 3 2011 | |||
| ||||
| Revision 0.1-1 | Wed May 12 2010 | |||
| ||||